Modernisation becomes meaningful only after understanding the system you’re dealing with. In Part 1, we mapped what the business needs and assessed the complexity, risks, and boundaries of the legacy application. With that clarity, the next step is choosing the right modernisation strategy. Microsoft highlights that modernisation should be an iterative process of planning and incremental transformation rather than a single large redesign effort . This article focuses on the patterns and approaches that make that possible.
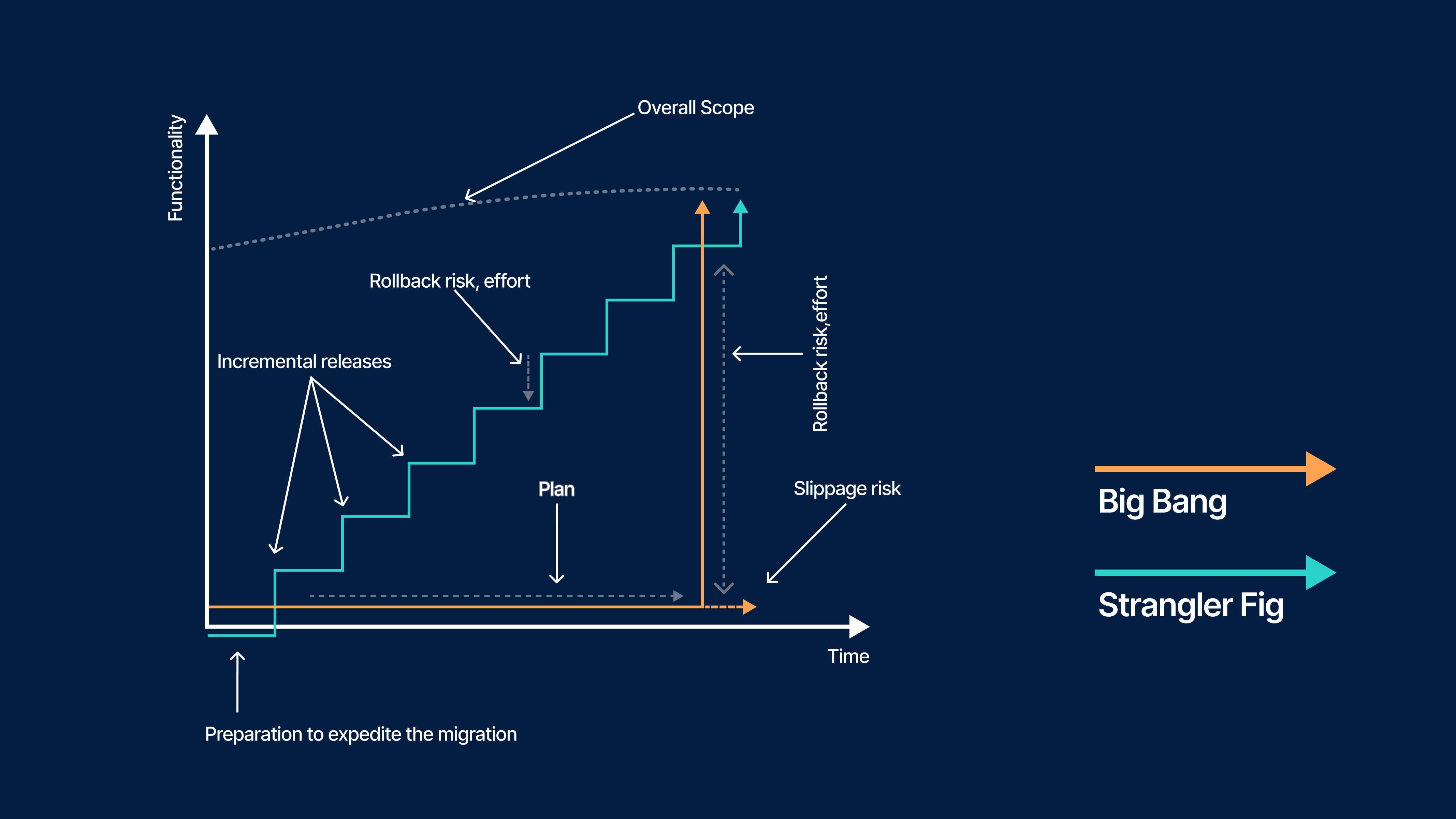
Big-Bang vs Incremental Modernisation
Modernisation efforts usually fall into two categories:
Big-bang rewrites replace everything in one go. They often fail due to long timelines, unclear requirements, and the difficulty of reaching feature parity before deployment. They may be justified only when the legacy system is fundamentally unsalvageable.
Incremental modernisation, however, replaces the system in manageable slices. It reduces risk, allows learning during the transition, and delivers value earlier. This approach aligns with practical engineering constraints and is compatible with patterns like Strangler Fig, modular architecture, and event-driven integration.
When teams can isolate capabilities, incrementally route traffic, and deliver new components piece by piece, incremental modernisation becomes the safer and more sustainable strategy.
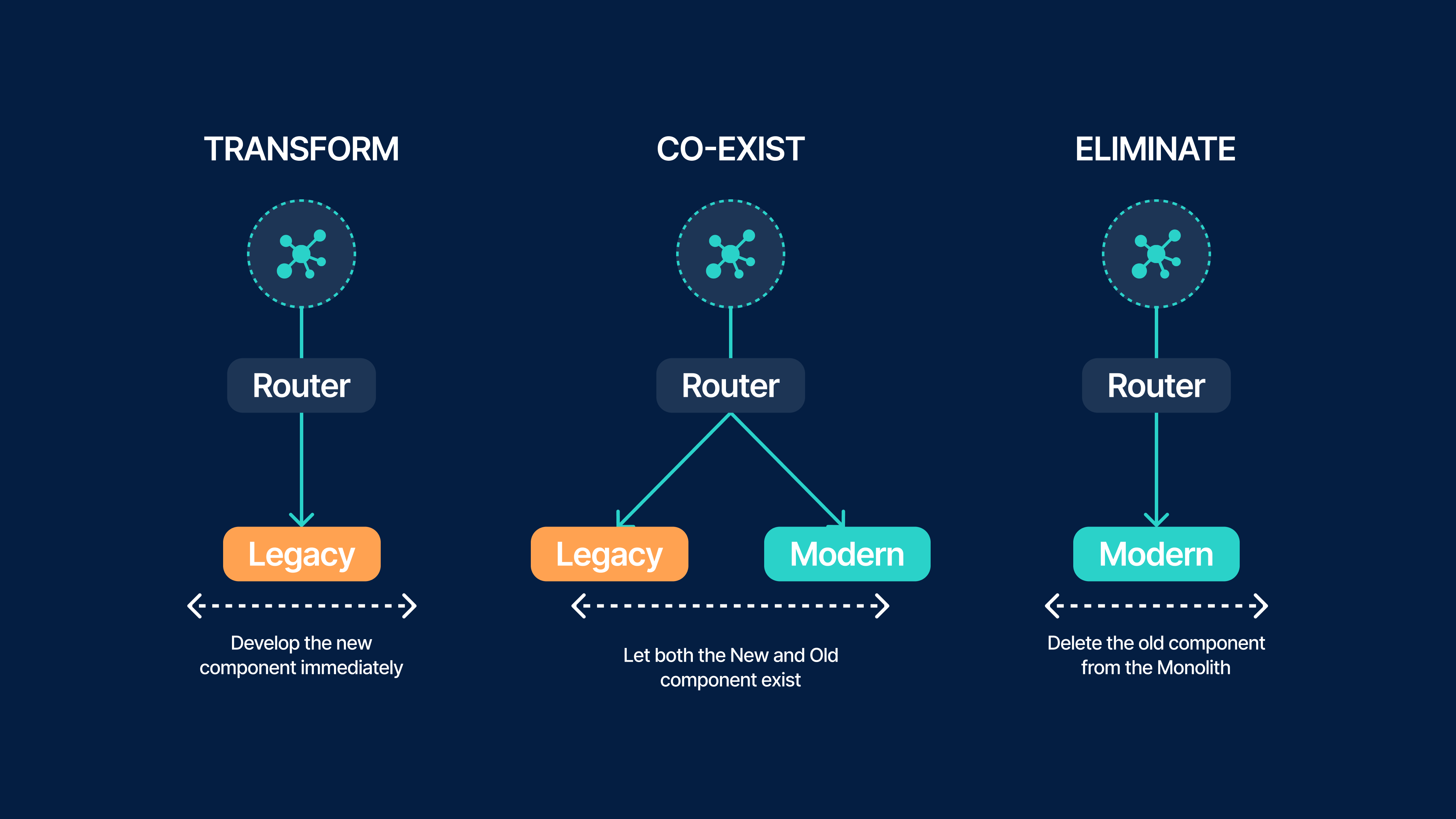
The Strangler Fig Pattern: Transforming Safely in Stages
The Strangler Fig pattern, originally introduced by Martin Fowler, “gradually replaces specific pieces of functionality with new applications and services” instead of rewriting an entire system at once . It is one of the most reliable modernisation approaches because it allows legacy and new components to coexist.
A typical application of this pattern involves:
- Introducing a routing layer or gateway
Requests flow through a central entry point that can forward traffic to the legacy application or new services. This creates a safe mechanism to redirect capabilities as they are modernised. - Extracting a capability into a new module or service
Once a clear functional boundary is identified—such as billing, reporting, or authentication—it can be implemented behind a new API, aligning with modern architectural practices: REST, gRPC, GraphQL, or messaging endpoints. - Synchronizing data between old and new boundaries
This step prevents inconsistent behaviour. Techniques such as change data capture, transaction outbox, or temporary dual writes help bridge legacy persistence models with modern read/write patterns. - Redirecting traffic to the new implementation
Once validated, the routing layer forwards calls to the new component while legacy pathways remain available as fallbacks if needed. - Repeating the cycle capability by capability
Over time, the legacy system is reduced until it can be safely retired.
The Azure Architecture Center also adopts this model as a recommended strategy for modernizing enterprise systems and cloud migration efforts .
Identifying Which Modules to Extract First
The success of incremental modernisation depends heavily on choosing the right boundaries.
Look for modules that are:
- Functionally cohesive
- Used frequently or are business-critical
- Loosely coupled to other parts of the system
- Painful to maintain or evolve
- Supported by clear workflows or available documentatio
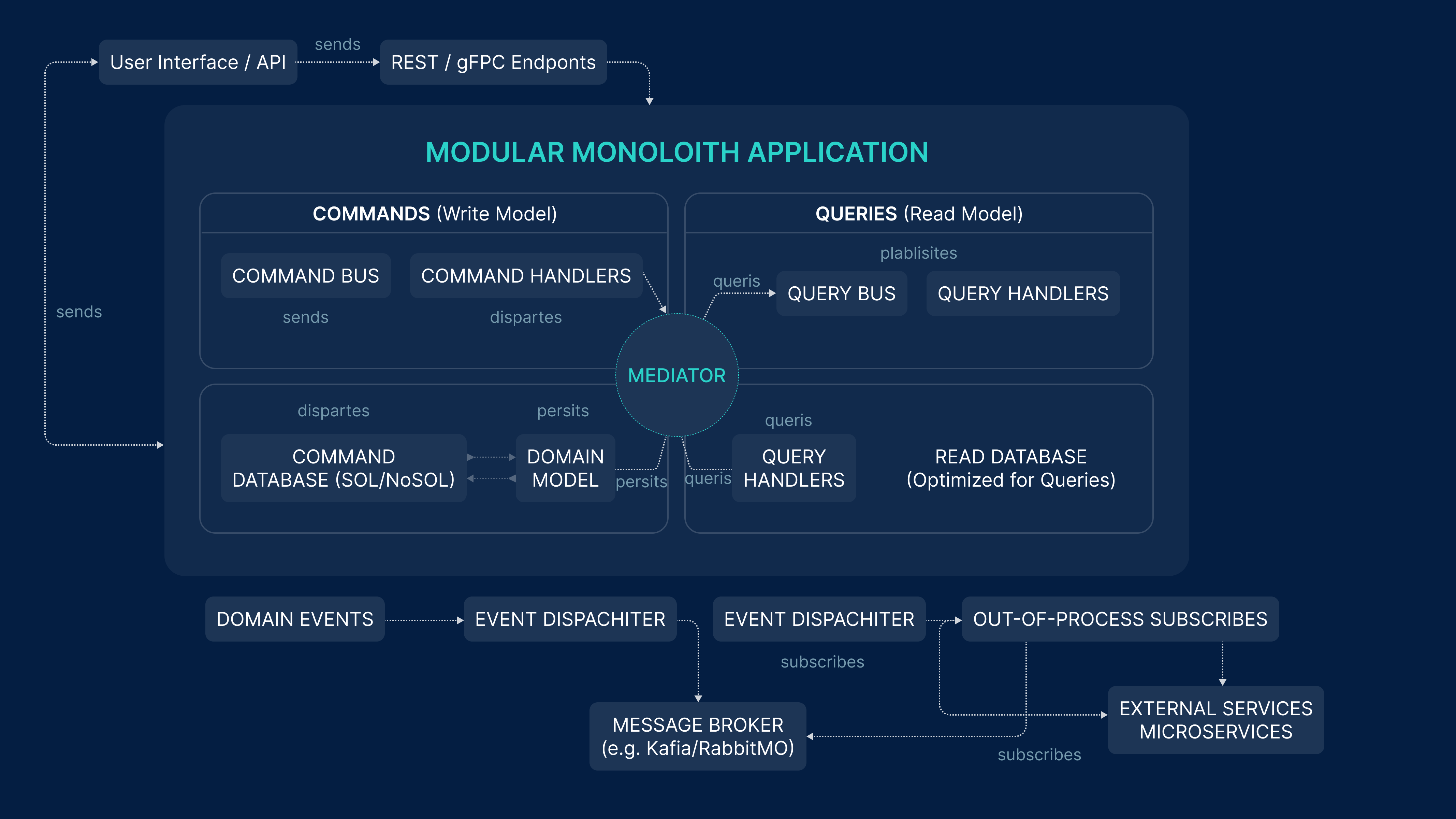
Splitting along domain boundaries aligns well with modern modular architectures and CQRS principles, even if you do not adopt full microservices. This allows development teams to introduce new APIs, event flows, or background processing without disrupting the entire application.
Boundaries chosen poorly can increase friction and introduce risk, while well-chosen ones accelerate the entire transformation.
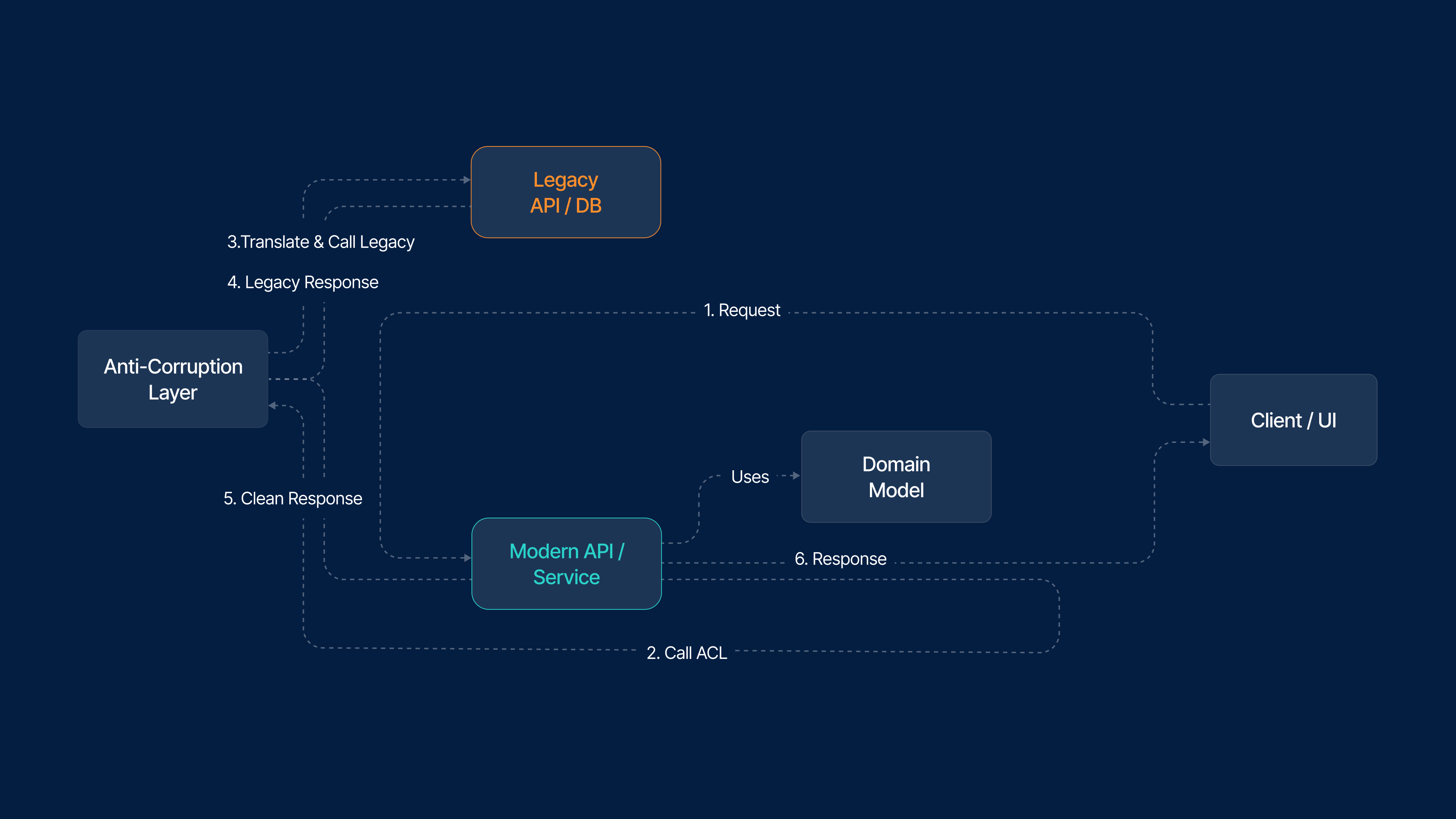
Anti-Corruption Layer (ACL) & Façade Patterns
When new modules must interact with legacy systems, introducing an Anti-Corruption Layer protects modern components from inheriting undesirable characteristics from the old design. ACLs translate data formats, flatten complex schemas, and standardise interactions so that new code operates with clean inputs and outputs.
Similarly, a Façade can be used to wrap legacy workflows into stable interfaces. This makes them easier to replace later without breaking dependent modules.
These patterns are especially important when the legacy system uses:
- custom or proprietary protocols
- non-idempotent operations
- shared database schemas
- outdated serialization formats
They ensure that modern code remains stable even while legacy components continue to operate in the background.
Data Migration Patterns for Modernisation
Data is often the most challenging part of modernisation. Poorly managed data transitions introduce inconsistencies, double-processing, or customer-facing errors.
Common strategies include:
- Dual Writes: Write to both the legacy and new data stores until confidence is built.
- Change Data Capture (CDC): Capture modifications from the legacy database and propagate them to new read or write models.
- Transactional Outbox: Ensure reliable event publishing from legacy operations through consistent transaction patterns.
- Backfill Processes: Rebuild new data models from historical legacy data in controlled batches.
Choosing the right approach depends on how tightly legacy uses its database and how critical real-time consistency is for your workflows.
Using Messaging and Background Processing for a Smooth Transition
Modernisation efforts benefit significantly from asynchronous communication. Patterns such as event publishing, domain events, and outbox mechanisms allow the new components to process work without relying on synchronous legacy calls.
This enables:
- decoupled interactions
- reduced load on legacy services
- background processing for data synchronization
- safe, incremental feature rollout
Most modernisation-friendly architectures combine synchronous APIs (REST/gRPC) with asynchronous pipelines (messaging, background services, scheduled tasks) to deliver a more resilient transition.
Managing Risk During Migration
Migration introduces several risks—data divergence, inconsistent behaviour, security gaps, or unclear ownership between old and new systems. OWASP highlights that legacy ecosystems often contain outdated components and insecure integration points, which must be addressed during modernisation .
Effective risk management practices include:
- maintaining fallbacks through routing and feature flags
- keeping legacy and new modules versioned and monitored
- validating data consistency at each migration step
- adopting incremental rollouts with canary or dark-launch testing
- ensuring operational observability (logging, metrics, tracing) across both systems
When applied consistently, these practices significantly reduce the uncertainty associated with migrating critical functionality.
Closing Thoughts
Modernisation is not a single architectural choice—it is a sequence of coordinated decisions. Patterns like the Strangler Fig, anti-corruption layers, and event-driven integration help teams evolve legacy systems without the risk of a full rewrite. By selecting the right boundaries, preparing data migration pathways, and managing risk deliberately, teams can modernise safely and sustainably.
In Part 3, we’ll explore how to choose the right technology stack to support the modernisation strategy—ensuring compatibility, long-term maintainability, and architectural flexibility.
References
- Microsoft — Application Modernisation Lifecycle (assessment → planning → execution → optimization)
- Martin Fowler — Strangler Fig Pattern
- Azure Architecture Center — Strangler Fig migration strategy
- OWASP — Legacy System & modernisation-related security concerns